This article is the continuation of Rails + Sidekiq + Docker Application for AWS (ECS, ECR, RDS, Codepipeline and more) complete series. For better understating, please start from the beginning of the series.
We have successfully created our rails application with Docker and Docker Compose along with MYSQL and Sidekiq (using redis) for our development environment. Now we plan to put our website on AWS using (ECR, ECS, RDS, Elastic Cache and Load Balancer etc).
Disclaimer: We will do a lot of configuration in this article. It may look time consuming but it will lay the foundation for all the communication such as Rails website with MYSQL and Sidekiq storage.
Security Groups
We will be creating the Security Groups for the following services:
- Load Balancer
- EC2 instances (Rails application and bastian host)
- RDS (MYSQL)
- Elastic Redis Cache (for Sidekiq)
I have created these Groups having security in mind, we should not open any unnecessary port on any service.
Login to your AWS console and click on EC2 from the Services menu, we will take notes of the security groups IDS while we create them.
From EC2 console, click on Security groups
Security Group for Load Balancer
The first Security Group is for the Load Balancer. For outside world, it will enable HTTP (Port 80) in the Inbound Rules. Please select the Inbound tab and click on Add Rule.


Security Group for Bastian instance
We will create a Bastian EC2 as well, the reason for doing that is we should be able to connect to our rails application, rds and redis cache etc for testing or troubleshooting.
Create another Security group do the following
Security Group for Rails Application
In this Security Group, Our goal is to allow Load Balancer and Bastian in Inbound rules. You need the Group ID of Bastian and Load balancer Security groups created earlier.
Let’s create this Security Group.
Load Balancer can connect to the rails application on all TCP ports and bastian instance can connect to rails application instance on port 22 only
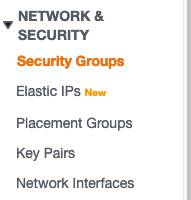
Security Group for RDS (MYSQL)
This Security group enables Rails Application and Bastian to connect to RDS using port 3306
Security Group for Elastic Redis Cache (for Sidekiq)
This Security group enables Rails Application and Bastian to connect to Elastic cache (redis) using port 6379